Avoid getting hacked 101: A guide to secure passwords
To create more secure logins, it's advisable not to use a password that contains publicly available details. Always ensure your passwords contain a random series of text and symbols.

Editor's note: This is a multi-part series about staying safe online. Lesson one explores passwords with tips on how to secure them.
"Someone has hacked my Facebook account", said Dele*, an older relative.
According to him, the hackers made subtle changes to his profile. "Subtle" because Facebook uses a Safeguard that doesn't allow users to enact multiple significant changes in a short time unless it's a flagged account.
The hacker started by changing the details of what Dele likes; books, movies and even joined new Facebook groups with Dele's account. Afterwards, the hacker changed Dele's profile name. It was at that point that Dele realised that he had been pwned (translates to "owned" AKA "hacked").
But just how were the hacker(s) able to gain access into his account. As part of my investigation, I did the following:
- checked the third-party applications connected to his Facebook,
- scanned his computer for malware
- checked if his email address was part of any known password leaks
None was positive. I then asked what Dele used as his password...ah, that must have been it!
It's 2019 and stories of cybersecurity breaches are all too familiar. From password breaches to social media hacking, we've seen it all. One does not merely use a password that contains the year of birth and children's name; it is too "brute-forcible".
Passwords are the current gateway to our online world
Despite its frailties, passwords are the preferred mode of authorisation on most online platforms. There is a password for Twitter, Facebook, Email and even internet banking.
As such, users have to take on the burden of creating memorable passwords. The popular thinking is that so long our passwords are safe and known to just us, outsiders shouldn't be able to access our accounts. However, passwords have been around long enough to have standard ways of hacking them. A hacker can more easily brute-force a user's password with dictionaries and word-lists. So, users with a simple password like "password" or one with their name and year of birth like Dele are easy targets.
Brute-force is a trial-and-error method used by hackers to guess a user's password or PIN. This article explains the process in more depth.
7 tips for securing our not so secure passwords
Here are seven easy-to-follow ways you can secure yourself online via the use of passwords:
1. Avoid dictionary words
Whenever hackers try to guess a user's password, they brute-force the account details using one or a combination of the following:
- A dictionary list which is a list of words or commonly used passwords like "password"
- Random guess using publicly available details of the user, like your date of birth, and names which can easily be gotten from your social media accounts like Facebook
To create more secure logins, it's advisable not to use a password that contains publicly available details. Always ensure your passwords contain a random series of text and symbols. To make is easier, you can use this password generator.
2. Do not repeat your password across platforms
This an issue most users are guilty of, as a lot of people reuse their passwords across multiple sites. It is bad practice to use the same passwords for your banking application and your social media sites or any other website that requires a password.
Every now and again we hear of a data leak, if you are a user that repeats passwords, a breach of one of the websites with your login details could spell doom for you because it would inevitably give hackers access to all your other accounts.
3. Avoid commonly-used passwords
If your password is ‘password’ or ‘12345678’, it would take even an amateur hacker 10 seconds or less to gain access to your account.
Hackers use information from previous password dumps as dictionaries when trying to brute force user accounts. Every year, a list of the most used passwords change but only just a little, the NCSC (National Cyber Security Centre) for the UK published a list of the top 100,000 most used passwords for the first quarter of 2019. They are listed below:
- 123456
- 123456789
- qwerty
- password
- 111111
- 12345678
- abc123
- 1234567
- 12345
Here is a link to the full list of the 100,000 most used passwords, commonly appearing details like your name or the name of your favorite football club aren't advisable. Be creative, use random words or just use a password generator.
4. Use a Password Manager
Remembering a lot of random passwords for different websites can be a bit of a hassle (unless you are Sherlock Holmes). There is a limit to the amount of random information you can remember.
A Password manager is an application that assists in the generating, storing and retrieving of complex passwords. It stores these passwords in a database (that is encrypted with your master password) or is able to generate them on-demand.
Password managers like LastPass or 1Password offer both a free and a paid version but for regular users, the free version of these password managers should be enough. They support major platforms, from iOS and Android apps to Desktop applications and browser extensions.
Password managers also help you login automatically to the websites you use.
5. Do not login or enter sensitive information on an unencrypted site.
On the internet, there are a vast number of websites offering various services, these sites transfer content to and fro our devices to web servers. The data can be interrupted in-transit using an MITM attack (a man-in-the-middle attack), if the information tunnel isn't encrypted.
This is why secure practice demands that websites use HTTPS which is HTTP (HyperText Transfer Protocol) plus SSL (Secure Sockets Layer) to securely transfer and display content over the internet.
HTTPS = HTTP + SSL
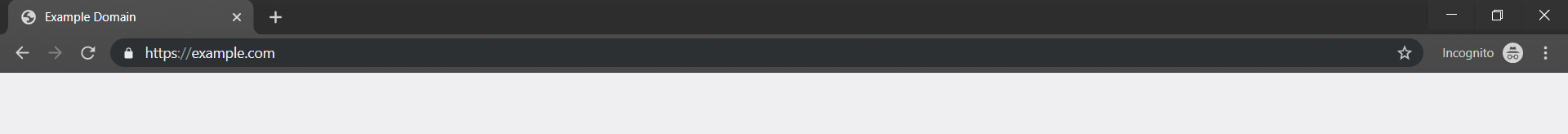
The padlock shown next to the url in the url bar tells us that our connection to the web server is encrypted
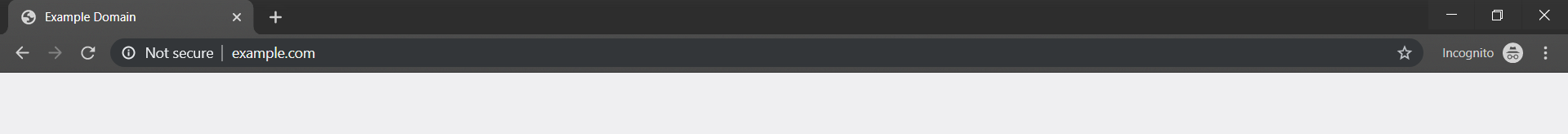
Also, when surfing the internet or visiting sites that contain sensitive information, be careful with links and ensure the sites we are visiting has HTTPS enabled so hackers spying on network traffic wouldn't be able to view our data in plain text (that is, unencrypted).
6. Reduce oversharing on social media, whether it was solicited or not
Drop your phone number for data if it's MTN or GLO. I will choose 30 people. No Davido fans. I read everyone's comment. Have a great week👍🇳🇬
— Nigerian Journalist Kemi Olunloyo🕸️ (@HNNAfrica) April 28, 2019
Drop your account number and Retweet. Let me surprise a few people 😊
— Edwin ℳasobeji (@madeinmwanza) December 19, 2018
3. When is your birthday ?
— KRISTIAN 💗 (@MoanKrissy) April 28, 2019
2. How old are you ?
— KRISTIAN 💗 (@MoanKrissy) April 28, 2019
Stop naively sharing personal information on the internet. Many of these are used as security questions in the event that you forget your password and demand a reset.
Knowing this, a hacker could simply add you on Facebook or any other social media platform and lurk around for you to voluntarily share this information on there. Once he/she gets that, they can then pose as you and demand a password reset, filling out the correct answers to the security questions, where needed.
Don't reply to a Twitter thread that asks for your mother's maiden name. (Like why do people fall for these silly tricks, haba.).
In addition, learn to use long random answers for your security questions. Plus, you can also save the answers in your password manager if remembering them each time would be difficult.
7. Use 2FA (Two-factor Authentication), where available
One of the best methods to protect our online accounts is the use of 2FA AKA Two-factor Authentication. This is an extra layer of security that helps to ensure that the person trying to log-on to an account is the rightful owner of said account.
Let's use one of the most popular instances of 2FA in Nigeria—online banking.
Most users of online banking in Nigeria are given a hardware device that they use to generate a token to authorize transactions from their account.
Two-factor authentication can come in various ways:
- It could be information that should be personal to you: a secret question, or a PIN
- It could be the hardware you have: your phone or a hardware token
- It could be something you are: a biometric scan (fingerprint/touch ID), or Iris/Face Recognition
In conclusion, passwords are here to stay and until a more secure means of authentication becomes widely accepted—perhaps, passwordless logins. Users can protect themselves online by choosing more secure and random passwords, avoiding commonly-used passwords, and staying away from unsecured sites.
This article was edited by Benjamin Dada
Subscribe to never miss an article from benjamindada.com.
*Dele is not his real name







Comments ()